PTaaS vs Traditional Penetration Testing: Key Differences and Advantages
Understanding Penetration Testing as a Service (PTaaS) Penetration Testing as a Service (PTaaS) is a modern, cloud-based approach to penetration testing that provides continuous and real-time assessments of an organizations security. Unlike traditional penetration testing, usually a one-time event, PTaaS delivers ongoing support, helping businesses stay protected against ever-changing threats. PTaaS combines the best of automated tools and manual testing by security experts.

PTaaS vs
Traditional Penetration Testing: Key Differences and Advantages
The importance of cybersecurity has never been greater. As
organizations expand their online presence and rely more on technology to drive
operations, the risks associated with cyber threats are on the rise. From data
breaches to sophisticated attacks, businesses must be prepared to protect their
sensitive information and systems.
One of the most effective ways to safeguard an
organization’s cybersecurity posture is through penetration testing. However,
as cyber threats continue to evolve, so too must the methods used to detect
vulnerabilities. This is where Penetration
Testing as a Service (PTaaS) comes into play. PTaaS is a modern,
service-based approach to cybersecurity assessments, offering businesses
continuous, scalable, and integrated testing solutions. Unlike traditional
penetration testing, which typically offers a one-time snapshot of security
vulnerabilities, PTaaS delivers ongoing security evaluations, ensuring your
systems are always protected.
By embracing PTaaS, organizations can stay ahead of emerging
threats, improve their security measures, and maintain a proactive stance
against cyberattacks.
The Basics
of Traditional Penetration Testing
Building strong cybersecurity starts with understanding
where your defenses are weakest. Traditional penetration testing, often called
ethical hacking, is a trusted method where skilled professionals simulate
real-world cyberattacks on an organization’s systems, applications, and network
infrastructure. The main purpose is to uncover vulnerabilities before malicious
hackers can exploit them.
Traditional penetration testing usually follows a structured
process, which includes:
● Planning and Reconnaissance: Gathering detailed information
about the target environment, including systems, applications, and network
structures, to prepare for testing.
● Scanning: Using specialized tools to find vulnerabilities across
networks, servers, and applications.
● Exploitation: Attempting to breach systems by actively exploiting
identified weaknesses, showing what a real attacker could achieve.
● Post-Exploitation: Determining the potential impact
by maintaining access and assessing how much damage a successful attack could
cause.
● Reporting: Delivering a full report with findings, detailed risk
analysis, and clear recommendations for fixing the vulnerabilities discovered.
While traditional penetration testing is critical for
understanding and improving security, it also has some important limitations.
Since these tests are usually performed once or twice a year, they only offer a
snapshot of the organization’s cybersecurity at that moment. As new
vulnerabilities emerge quickly, this gap can leave businesses exposed between
testing cycles.
At SafeCybers.ai, we believe that
while traditional pen testing remains essential, businesses today need faster,
more flexible services and that’s where modern approaches like PTaaS come into
play.
Understanding
Penetration Testing as a Service (PTaaS)
Penetration Testing as a Service (PTaaS) is a modern,
cloud-based approach to penetration testing that provides continuous and
real-time assessments of an organization's security. Unlike traditional
penetration testing, usually a one-time event, PTaaS delivers ongoing support,
helping businesses stay protected against ever-changing threats. PTaaS combines
the best of automated tools and manual testing by security experts, creating a
more flexible and responsive way to find and fix vulnerabilities. Key features
of PTaaS typically include:
● Continuous Testing – Regular security assessments that
keep pace with new threats and system changes.
● Cloud-Based Platforms – Scalable solutions that grow with
your IT infrastructure, making it easier to secure expanding digital
environments.
● Integration with Development Lifecycles – PTaaS can be built into your
Continuous Integration and Continuous Deployment (CI/CD) pipelines, ensuring
that security is considered at every stage of software development.
● Automated and Manual Testing – A powerful combination of
automated vulnerability scanning and expert manual testing ensures thorough
security coverage.
PTaaS offers businesses a more flexible, cost-effective, and
scalable alternative to traditional penetration testing. At SafeCybers.ai, we help companies strengthen their defenses by
delivering PTaaS services that are designed for today’s fast-moving
cybersecurity landscape.
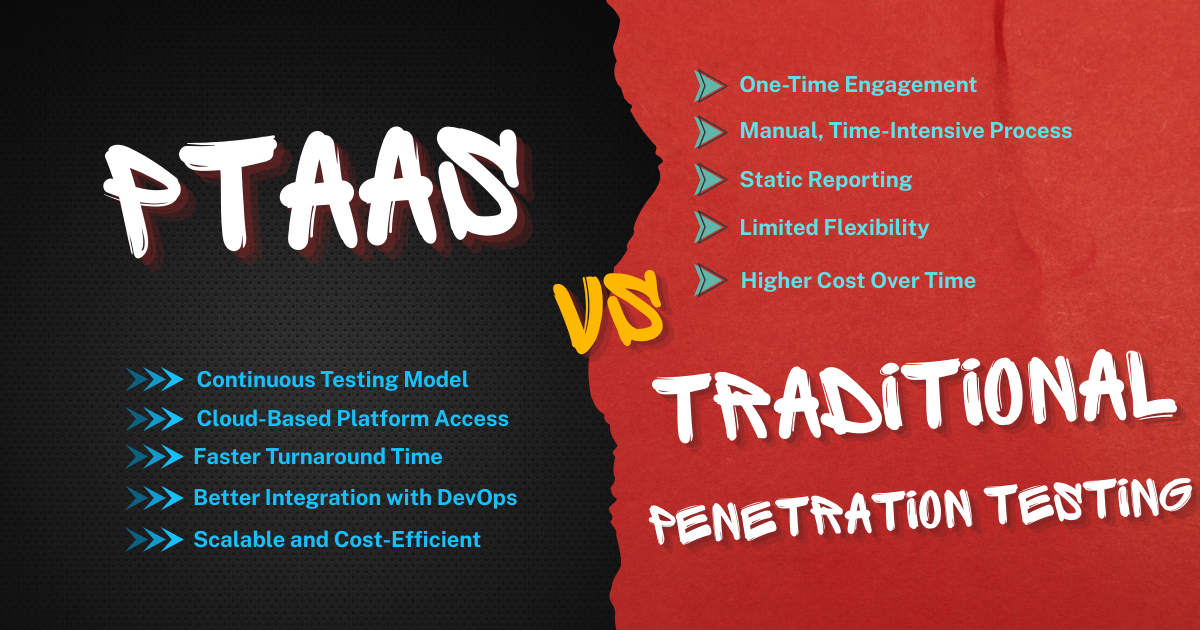
Key
Differences Between PTaaS and Traditional Penetration Testing
1. Delivery
Method
● Traditional Penetration Testing: This is a project-based service. A
cybersecurity team performs a penetration test over a few days or weeks,
delivers a report, and their work usually ends there.
● PTaaS: PTaaS delivers penetration testing on an ongoing basis
through an online platform. It combines expert testing with real-time results
and communication. You can view findings, updates, and recommendations anytime,
through a secure dashboard.
2. Speed and Flexibility
● Traditional Penetration Testing: Scheduling, scoping, and completing a
traditional test can take weeks or even months.
● PTaaS: PTaaS is much faster. Testing can begin quickly, and results
come in as soon as vulnerabilities are found. You don't have to wait for a
final report.
3. Cost Structure
● Traditional Penetration Testing: Typically charged as a one-time
project fee. If you need another test later (for example, after updates or
patches), you have to pay for a new project.
● PTaaS: Usually offered as a subscription. This makes costs more
predictable and easier to plan in your cybersecurity budget.
4. Engagement and Communication
● Traditional Penetration Testing: Communication is often limited to
kickoff calls, periodic check-ins, and a final presentation of results.
● PTaaS: It offers ongoing
communication. You can ask questions, request re-tests, and get advice
throughout the entire subscription period.
5. Remediation Support
● Traditional Penetration Testing: Once you receive your final report,
support may be limited. You may have to handle fixing vulnerabilities on your
own or pay extra for consulting help.
● PTaaS: Most PTaaS providers offer built-in remediation guidance.
They help you fix the issues faster, sometimes even testing patches immediately
after they are applied.
Advantages
of Traditional Penetration Testing
Traditional penetration testing has proven its value over
the years. It remains a trusted tool for businesses that need to find and fix
critical security flaws. Some of the main advantages of traditional penetration
testing include:
➢ Thorough, In-Depth Testing: Traditional pen tests are often very
detailed. Security experts carefully review systems to find serious,
high-impact vulnerabilities that might otherwise be missed.
➢ Expert Insights: Traditional penetration tests are
performed by skilled ethical hackers. These experts use real-world attack
techniques to show how an attacker could break into your systems. This gives
businesses a deeper understanding of their risks.
➢ Regulatory Compliance: Many industries require periodic
penetration testing to meet legal and regulatory standards. Traditional testing
helps businesses stay compliant with important rules like PCI-DSS, HIPAA, and
others.
While traditional penetration
testing offers strong benefits, it is usually a one-time event. It does not
provide real-time or continuous protection against new threats.
Advantages of Penetration Testing as a Service (PTaaS)
Penetration Testing as a Service (PTaaS) brings a modern
approach to cybersecurity. It offers many advantages over traditional methods,
making it a smart choice for today’s fast-moving businesses:
➢ Continuous Testing and Real-Time Alerts: PTaaS constantly monitors your
systems. Vulnerabilities are found as soon as they appear, allowing your team
to fix them quickly before attackers can take advantage.
➢ Cost-Effective and Scalable: PTaaS is often more affordable than
scheduling multiple traditional tests. Plus, it scales easily as your business
grows, without needing to add more internal resources.
➢ Seamless Integration with Development Processes: PTaaS can be built directly into
your DevOps or CI/CD pipelines. This means security checks happen automatically
during software development, reducing the chance of releasing vulnerable code.
➢ Actionable Reporting and Insights: Most PTaaS platforms offer
easy-to-read dashboards and clear reports. This helps your security teams
quickly understand what needs attention and what actions to take.
Which One is
Right for Your Business?
Choosing between traditional penetration testing and PTaaS
depends on the specific needs and resources of your organization. Traditional
penetration testing is ideal for businesses that need periodic, in-depth
assessments or those in industries with strict regulatory requirements.
However, if your business operates in a fast-paced environment, frequently
updates its systems, or requires constant monitoring, PTaaS is the better
choice. Evaluate your organization's needs, budget, and security goals to determine
which option best suits your business. It’s also worth considering that many
organizations are opting for a hybrid approach leveraging both traditional
penetration testing for in-depth assessments and PTaaS for continuous
monitoring.
As cyber threats continue to grow in both frequency and sophistication,
businesses must evolve their cybersecurity strategies. While traditional
penetration testing remains valuable, Penetration Testing as a Service (PTaaS)
offers a more dynamic, scalable, and continuous solution to protecting
sensitive information and systems. Organizations adopting PTaaS can stay ahead
of emerging threats, integrate security into their development processes, and
maintain a proactive security posture. As cybersecurity challenges evolve,
PTaaS provides businesses with the tools they need to secure their digital
assets and ensure long-term success.
Embrace the future of cybersecurity
with PTaaS and protect your business with Safecybers.ai. Contact us NOW!!.