0+
Clients Protection
An External Attack Surface Management can protect your Enterprise from hidden threats and give you peace of mind.
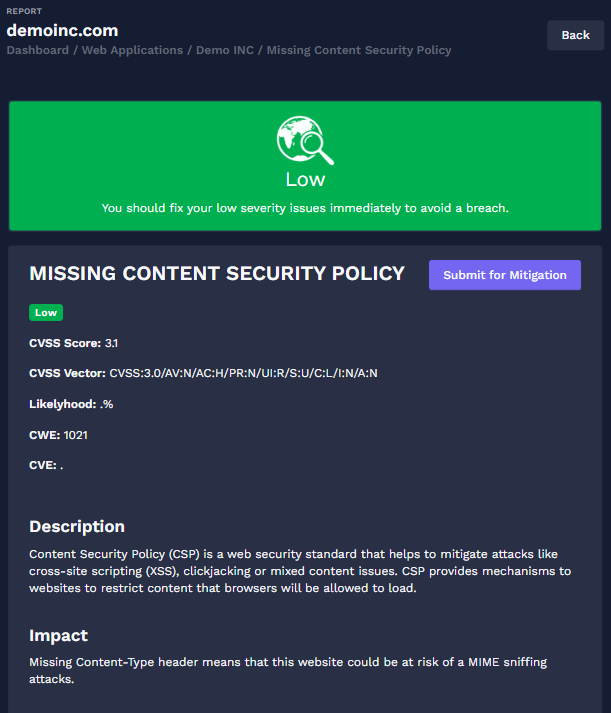
External Attack Surface Assessment, which is the process of identifying and addressing vulnerabilities in internet-connected systems. Assets including Web Application, Cloud Infra, Mobile Applications and API are included in this. By proactively detecting and resolving vulnerabilities in these external-facing systems, you can lower the risk of cyberattacks.
DISCOVER MORE
SAFE CYBERS AI a single platform that discovers, evaluates, and responds to vulnerabilities throughout an external attack surface while calculating a risk score. The SAFE CYBERS AI platform continuously scans and detects asset threats, vulnerabilities, and risks. Also, SAFE CYBERS AI platform does the intel analysis to prioritize exploitable risks.
DISCOVER MORE
Always on Pentesting that combines manual and automated testing with 24/7 scanning, consultation and streamlined communication and reporting delivered through a single AI platform. By delivering pentesting “as a service,” organizations receive a broader, more thorough vulnerability audit year-round instead of relying on one-time pentests, which are typically executed just once a year.
DISCOVER MORE

Improve your security with Darkweb Monitoring, which offers real-time warnings for data breaches, early detection to prevent hazards, and continuous deep web scanning for dangers pertaining to your brand.

When it comes to hacking, cybercriminals don't adhere to any rules, they'll enter by whatever means required. Hacker View protects your data by offering an inside look at potential exploits and insight into how hackers work.
Get a unique glimpse into your assets vulnerabilities from the eyes of a hacker. Identify potential security threats before they can be exploited.
Discover in-depth information about the attack surface and asset base of Enterprise, as well as potential entry points and weaknesses that hackers may exploit.



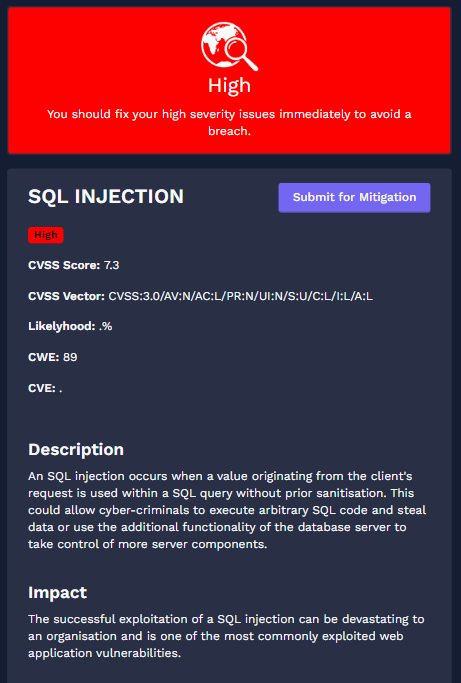
SafeCybers Cyber Threat Intelligence and real-world exploit data. This model produces a probability score. The likelihood that a vulnerability will be exploited increases with score.
Proactively identify and address potential security weaknesses before they become threats to your organization.
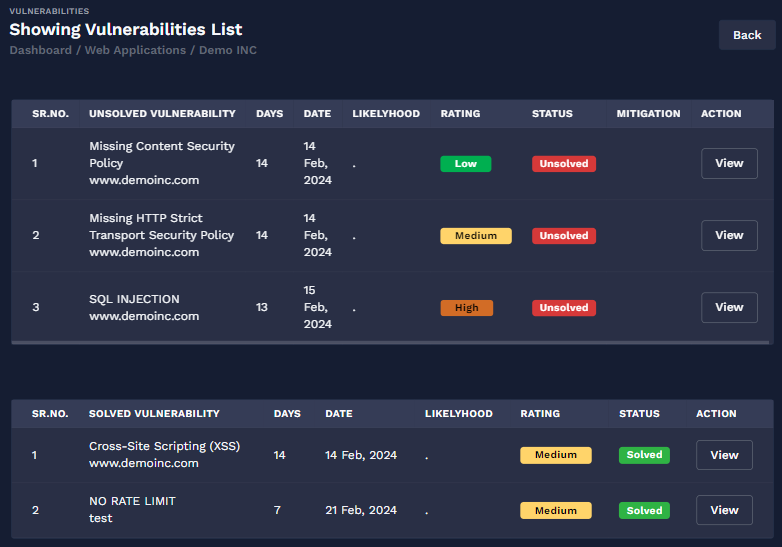
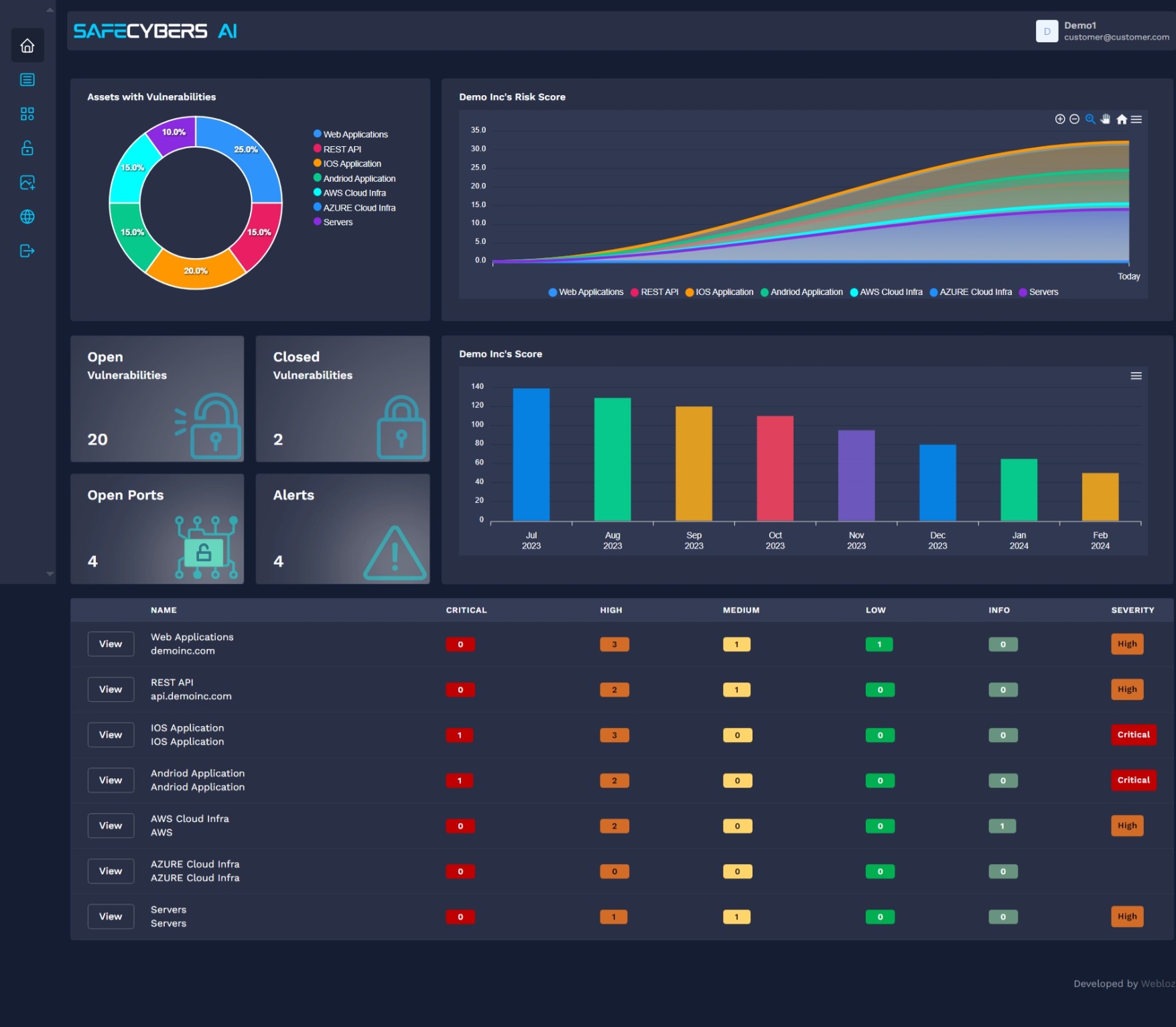
Identify vulnerabilities quickly with our user-friendly platform. SafeCybersAI offers an extensive summary of surface scan results.

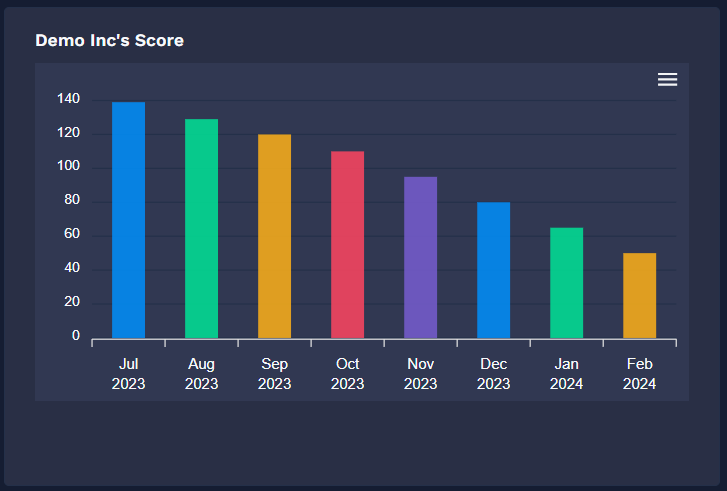
An organization's susceptibility to cybercrime and the liabilities resulting from IT vulnerabilities are determined by its cyber risk score. Everything from insurance prices to merger and acquisition chances might be impacted by a company's cyber risk score.
With the SAFECYBERS Cyber Risk Score driven by AI, you may acquire a clear understanding of the risk assessment of your apps and receive a thorough explanation of an organization's security posture.
Your quick and trustworthy tool for assessing cyber risk is the SafeCybersAI Cyber Risk Score. It evaluates risks, exposures, and vulnerabilities and converts them into an insightful statistic. With the help of this score, you can strengthen your cybersecurity and protect your digital assets by making wise decisions.
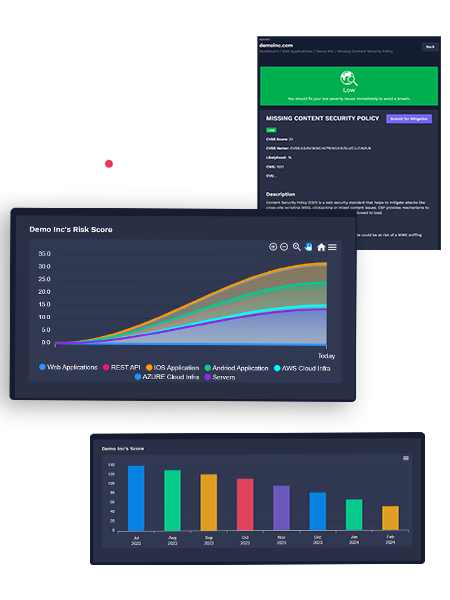
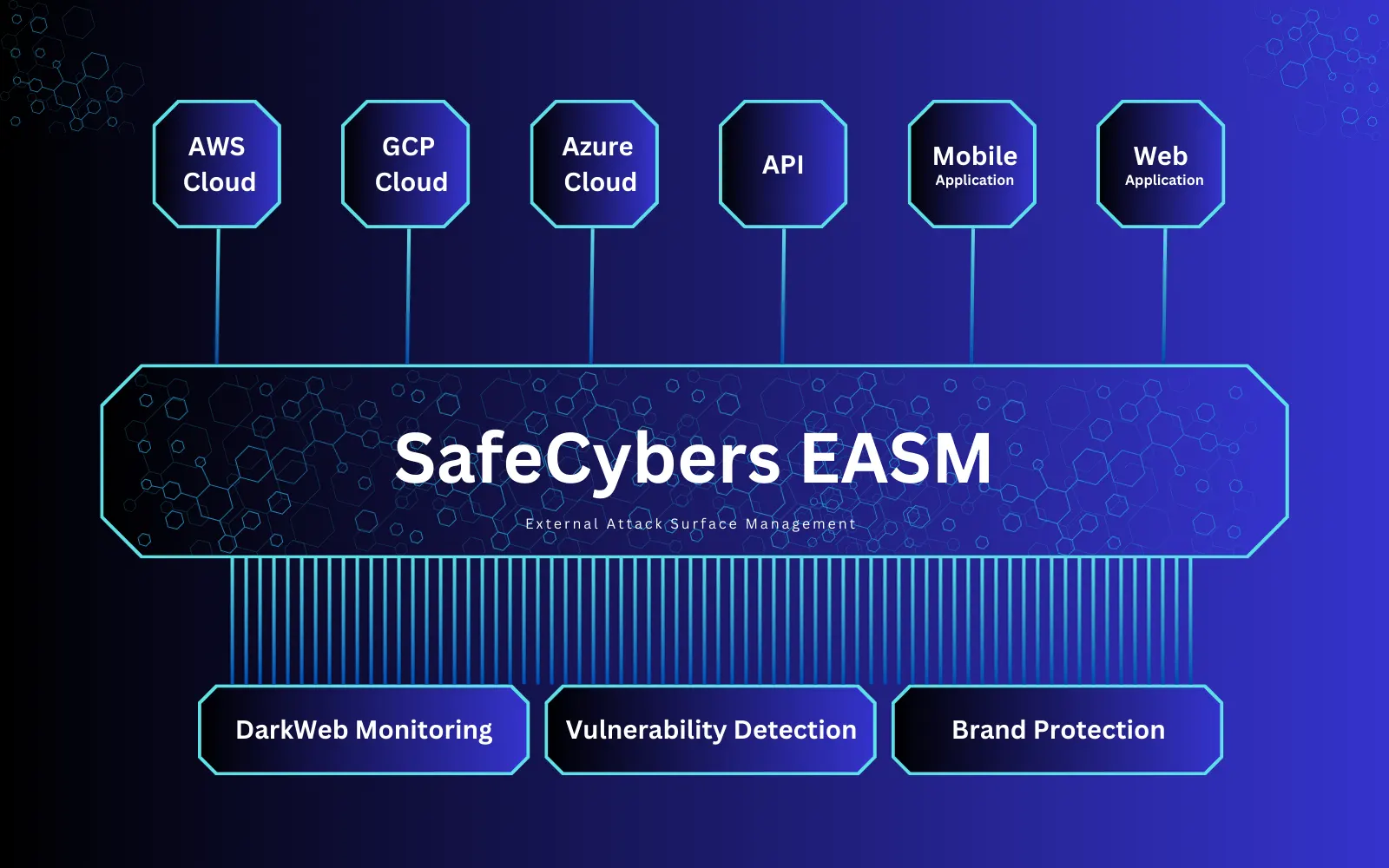









GS2's advanced solutions redefine digital transformation, enhance data management, and fortify asset protection with ease.
Presents a detailed view of potential threats existing within a system or application.
Spots programming errors which make the application prone to cyber attacks.

Ensures complete risk management and safeguards against external data threats.
Secures business from scenarios wherein reputation and money are at stake.
Safeguard applications, company data from internal, external and malicious attacks.
Many industry leaders already trust us for their security needs; join the ranks of our satisfied clients.
0+
Clients Protection
0 +
Projects Completed
0+
Website Protection
0+
Days Support
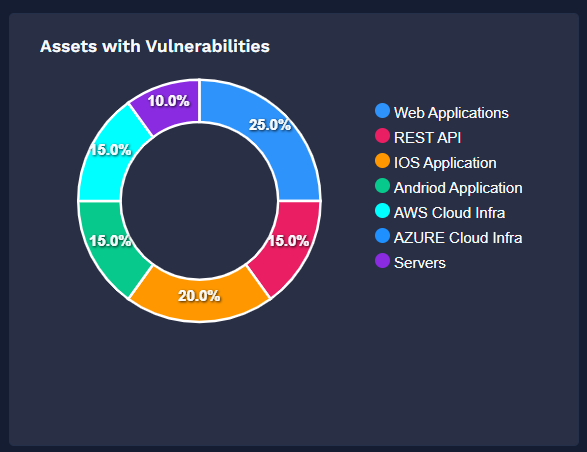
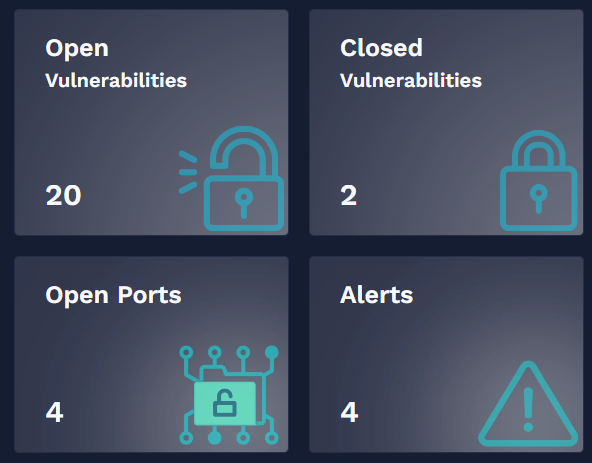
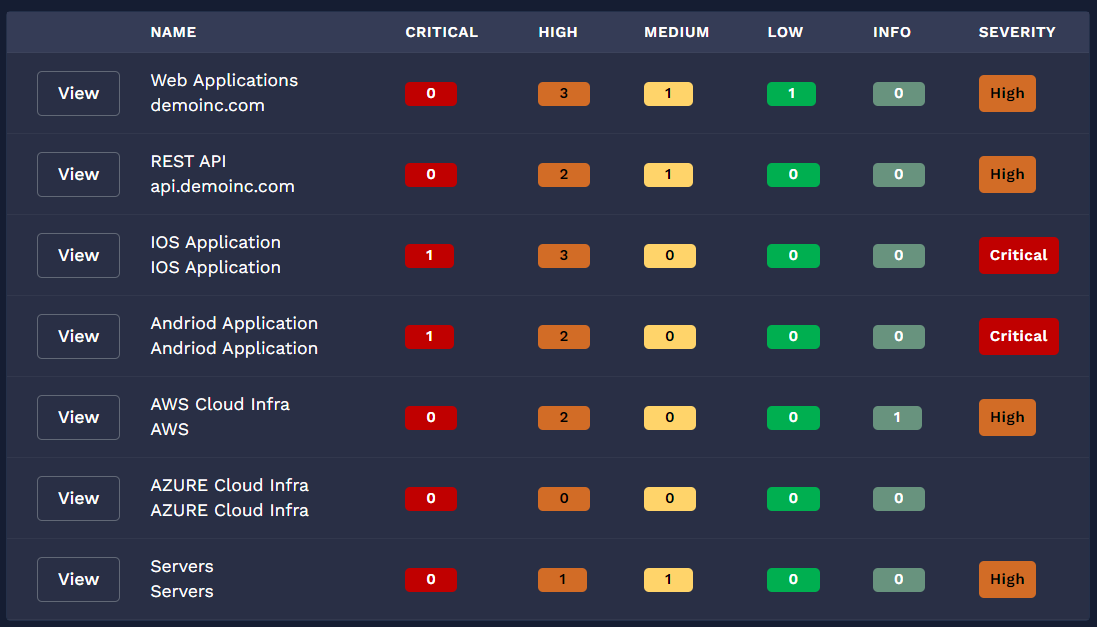
Hear from our satisfied clients about their experiences and Learn how our solutions have made our customers' businesses more secure and efficient.